Five Billion Cybersecurity Threats a Month, WhatsApp, Windows Hack, Intel Vulnerabilities

Note: McKenzie Worldwide has a strong cybersecurity practice. Here is a curated news roundup we produce for Cyber Oregon, a statewide initiative we helped launch and support on an ongoing basis. Drop us a line if you want to learn how we can help move your initiatives forward.
Is it possible for hackers to remotely hack into your mobile phone and steal your personal information just by calling your phone number? Unfortunately, the answer to that alarming question is yes for the 1.5 billion users who use the WhatsApp messaging application. Wired reports that the notorious Israeli spy firm NSO Group developed a WhatsApp exploit that could inject malware onto targeted phones – and steal data from them – simply by calling them.
According to a BBC article, WhatsApp hack: Is any app or computer truly secure, messages sent using WhatsApp are end-to-encrypted, meaning they are scrambled when they leave the sender’s device. However, messages can be read before they are encrypted or after they are decrypted. Spyware dropped on the phone by an attacker could read the messages.
Wired’s Lily Hay Newman writes that these zero-day bugs, in which attackers find a vulnerability before the company can patch it, happen on every platform. It’s part and parcel of software development. “Still, a hack that requires nothing but an incoming phone call seems uniquely challenging — if not impossible — to defend against,” she writes. This latest hack is another indicator that encryption and other such security measures offer protection and makes it much harder for attackers to read messages, but “cybersecurity is often a game of cat and mouse,” according to the BBC article. It states that any app could contain a security vulnerability that leaves a phone open to attackers.
This begs the question: is any device ever safe? It’s important for users to take action and install software updates for applications and operating systems, as they often contain software patches and fixes. Here are other preventative steps:
- Install app and operating system security updates
- Use a different password for every app or service
- Where possible, enable two-step authentication to stop attackers logging in to accounts
- Be careful about what apps you download
- Do not click links in emails or messages you are not expecting
Speaking of patches, this week Microsoft warned of a Windows bug that could lead to another WannaCry-size attack. The company has taken steps of patching Windows 2003 and XP.7, Server 2008, and 2008 R2. In Dan Goodin’s article in ArsTechnica, he writes that Microsoft warns that the Internet could see another exploit with the magnitude of the WannaCry attack that shut down computers all over the world two years ago unless people patch a high-severity vulnerability. The software maker took the steps of backporting the just-released patch for Windows 2003 and XP, which haven’t been supported in four and five years, respectively.
“This vulnerability is pre-authentication and requires no user interaction,” Simon Pope, director of incident response at the Microsoft Security Response Center writes. “In other words, the vulnerability is ‘wormable,’ meaning that any future malware that exploits this vulnerability could propagate from vulnerable computer to vulnerable computer in a similar way as the WannaCry malware spread across the globe in 2017. While we have observed no exploitation of this vulnerability, it is highly likely that malicious actors will write an exploit for this vulnerability and incorporate it into their malware.”
Rounding out this week’s vulnerability news, Intel shared details and information about a new group of vulnerabilities collectively called Microarchitectural Data Sampling. Zack Whittaker, in his TechCrunch article, writes that this secret-spilling flaw affects almost every Intel chip since 2011. These vulnerabilities, if exploited, can be used to steal sensitive information directly from the processor.
What could happen is hackers could exploit design flaws rather than injecting malicious code. Says Whittaker, “As more findings come to light, the data-stealing attacks have the potential to become easier to exploit and more streamlined.” Intel has released microcode to patch vulnerable processors. This article recaps the latest patches: https://techcrunch.com/2019/05/14/intel-chip-flaws-patches-released/
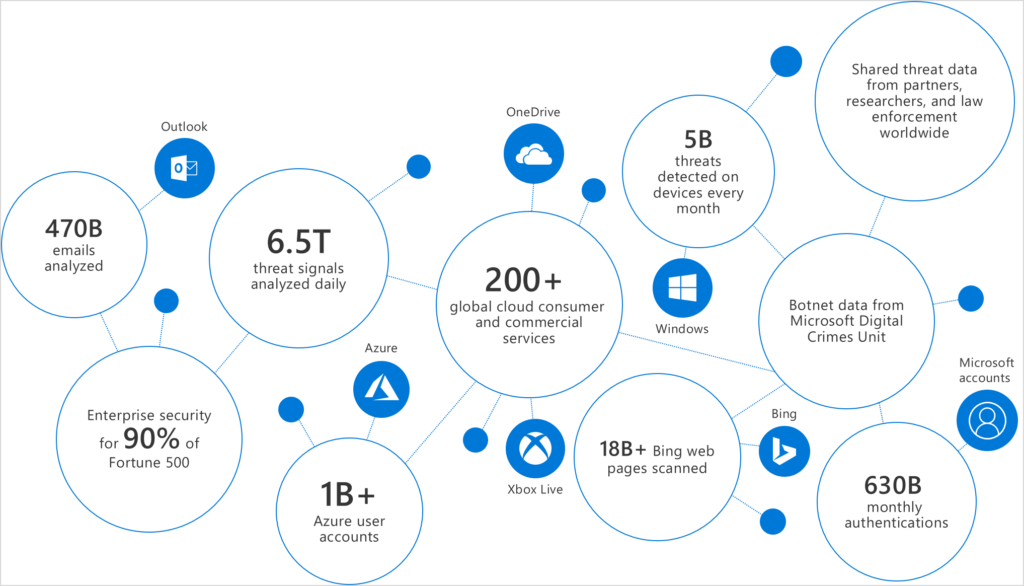
Five billion cybersecurity threats to devices each month
In other news, Microsoft has launched a new Microsoft Threat Protection website, where it is showcasing its Automated Incident response capabilities for SecOps teams, Azure Sentinel, and its human-powered Microsoft Threat Experts service. Microsoft reports that it detected five billion cybersecurity threats on devices a month.
According to a ZDNet article by Liam Tung, Microsoft is trying to connect the dots between various signals to develop threat alerts and provide organizations with a clearer picture of attacks that are underway, such as a phishing attack that could be targeting devices, email accounts or which could come via the web. Over the course of 2018, Microsoft analyzed 300,000 phishing campaigns and eight million business email compromise attempts, according to data from Office 365 security analysts.
How to stay ahead of the cybersecurity game
Susan Rebner, CEO of Cyleron, makes these recommendations for organizations to make cybersecurity and risk management a priority throughout the organization. In her Forbes article, she writes that cybersecurity is not just an IT issue — it extends to the entirety of the organization:
- Regularly communicate with your customers on your cybersecurity plans and how they will protect their data. Being fully transparent allows you to build trust.
- Do more than just the minimum antivirus software. Use multiple layers of protection. Go above and beyond to protect your customer data.
- Prioritize the data that needs protection and protect your organization’s crown jewels, such as customer payment details or private information. Understand where your greatest assets are located and take action to protect those assets in particular.
- Ensure that vulnerability testing is a common practice in your organization, not just penetration testing. Don’t wait to deal with threats until they occur; anticipate threats. Test, test, test and then test again.
- Educate your employees on cybersecurity best practices to create awareness and build a multilayer defense.
Additional cybersecurity resources available
Two new whitepapers are available to download from the Cyber Oregon website: https://cyberoregon.com/resources/#cyberpro
Center for Cybersecurity Policy and Law: To address concerns about security gaps across a growing number of connected devices, the Center for Cybersecurity Policy and Law has published a white paper designed to help hardware vendors minimize risks for end users.
The BSA Framework for Secure Software: BSA/The Software Alliance has developed The BSA Framework for Secure Software to provide a consolidated framework that brings together best practices in a detailed, holistic manner that can guide software security regardless of the development environment or the purpose of the software.
